NAT Types
When you're diving into peer-to-peer communication you'll most likely stumble upon STUN, ICE and NAT. I'm not diving into STUN and ICE in this article as they build upon some knowledge that I explain in this article. Below I'll explain on a high level how NAT works and the things you need to be aware of if you want to know more about peer-to-peer connections work. Note that I might leave out some details and simplify certain things. When you want to know more, you can have a look at some of the relevant RFCs.
What is a NAT
Before you continue, I assume you know about IP addresses and PORTs and that the PCs in your house have their own local range of IP addresses which are not share outside your router with the public Internet. A NAT is a device that is used to translate packets to and from your network with other networks. It's part of what makes the Internet the Internet.
At home you'll probably have router which functions as a NAT:
Network Address Translation. Your router which also functions as
a NAT will map internal addresses and ports to external ones.
When a packet arrives from the Internet to your NAT, the NAT uses
a table that maps the external extIP:extPORT to the
intIP:intPORT of the PC in your network that requested the
packet.
Types of NATs
Before diving into the different types of NATs it might give you a better understanding of NATs when you think about it like this: all these NAT types are related to how an external IP:PORT can send data to a PC behind a NAT. In most of these cases the NAT will check if the internal PC (behind the NAT) has already sent data to the external one. Based on this fact, the NAT will forward data to the internal PC where each different NAT type has different rules about how restrictive it is. E.g. some NAT types will reject incoming packets when the internal PC did not sent a packet to the external one.
There are generally four types of NAT which I'll describe in more detail below. The different types of NATs which I'll describe are:
- Full Cone NAT
- Address Restricted Cone NAT
- Port Restricted Cone NAT
- Symmetric NAT
Did the local PC already sent packets to the external one?
The above types of NATs will check if mapping has been created
already to determine how to deal with packets that the NAT receives
from the Internet. The image below shows a packet which is sent
from a local PC from a socket with an IP address locIp and port
number locPort to remote server on remIp:remPort.
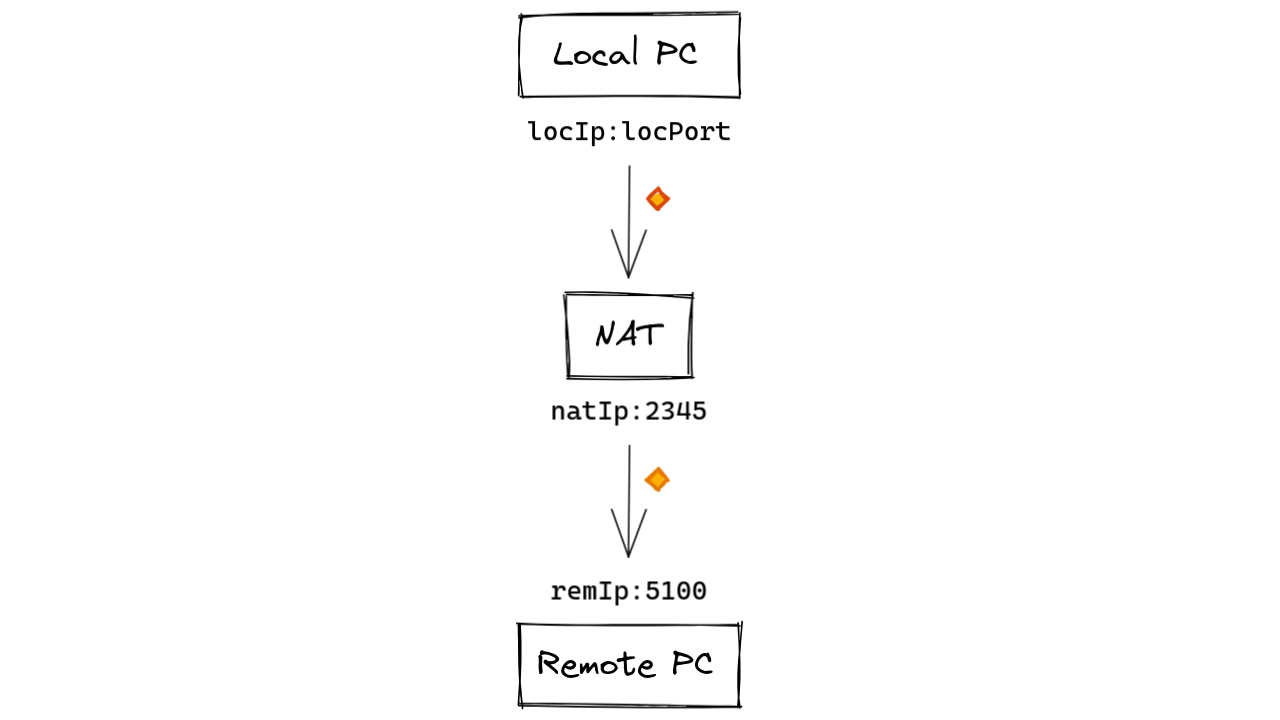 Image 1. The Local PC sends data to the remote PC port 5100, creating an address mapping.
Image 1. The Local PC sends data to the remote PC port 5100, creating an address mapping.
Full Cone NAT
I think the Full Cone NAT is the most simple one to understand as
it's similar to something you've dealt with in the past. Maybe
this is something that you've done before: creating a port
forwarding rule for an internal service. In your router or NAT
you've configured that when someone sends a request to port 80 of
your NAT/router IP address, that it will be forwarded to a local
IP and PORT. When you've created such a rule, you've
configured a (static) rule for a Full Cone NAT. With Full Cone
NAT devices, these rules are created automatically.
Ever created a port forwarding rule?
Nice, then you already know what a Full Cone NAT is.
In the image below you can see that any external host can sent a
message to the IP:PORT of your NAT and that the NAT will forward
it to the local PC. As long as an port fowarding rule exists this
will work and is called a Full Cone NAT.
In this particular case, the NAT device will not check if the local PC already sent a message to the remote PC. The following NAT types, Address Restricted NAT and Port Restricted NAT will check if the local PC already sent a packet to the remote PC or not.
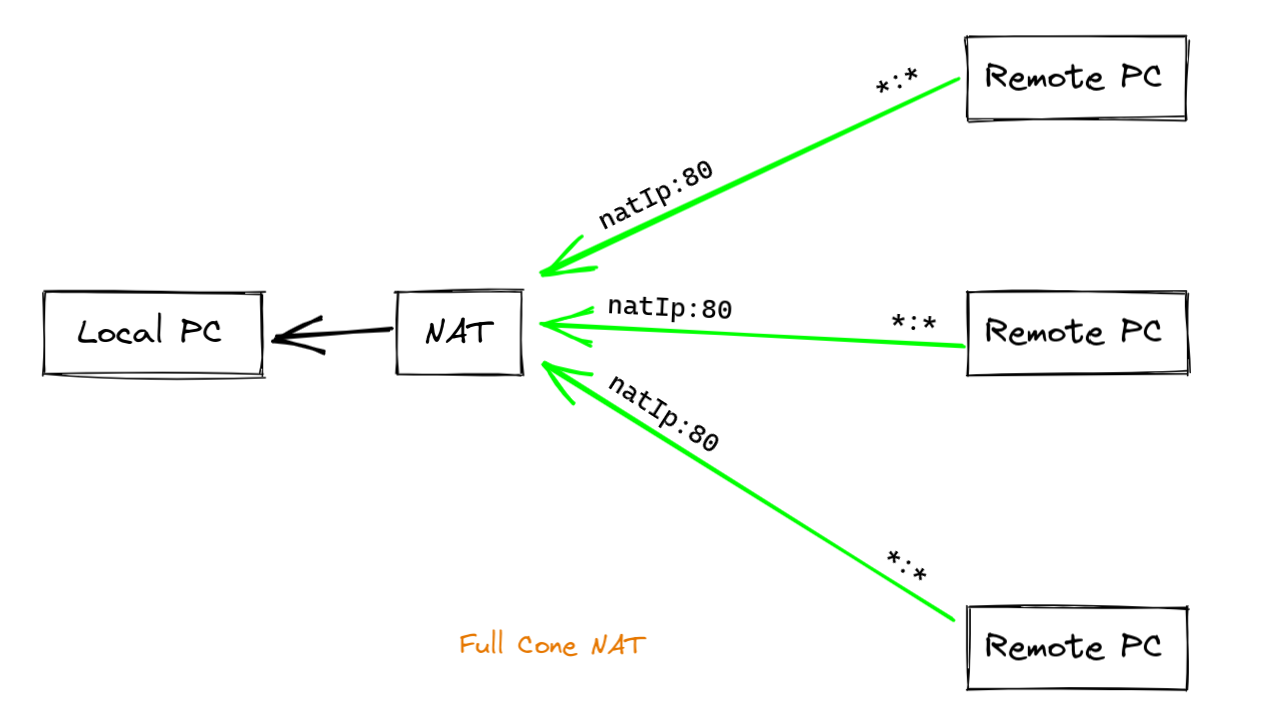 Image 2. With Full Cone NAT, the device allows traffic from any remote host
Image 2. With Full Cone NAT, the device allows traffic from any remote host
Address Restricted Cone NAT
While the Full Cone NAT is the most basic and well known NAT type, there are other types which are often used but which are less well known. I'm sure that you've created a static port fowarding rule yourself (i.e. Full Cone NAT rule). These other types are less known because they often apply to rules that are created automatically by your NAT device. This is also the case for the type I'll explain here: Address Restricted Cone NAT.
The Address Restricted Cone NAT will allow traffic from a remote
PC only when the local PC has previously sent data to this remote
PC. This is demonstrated in the image below. In this case we
assume that the local PC has sent data to the remIP:5100 port
as shown in image 2.
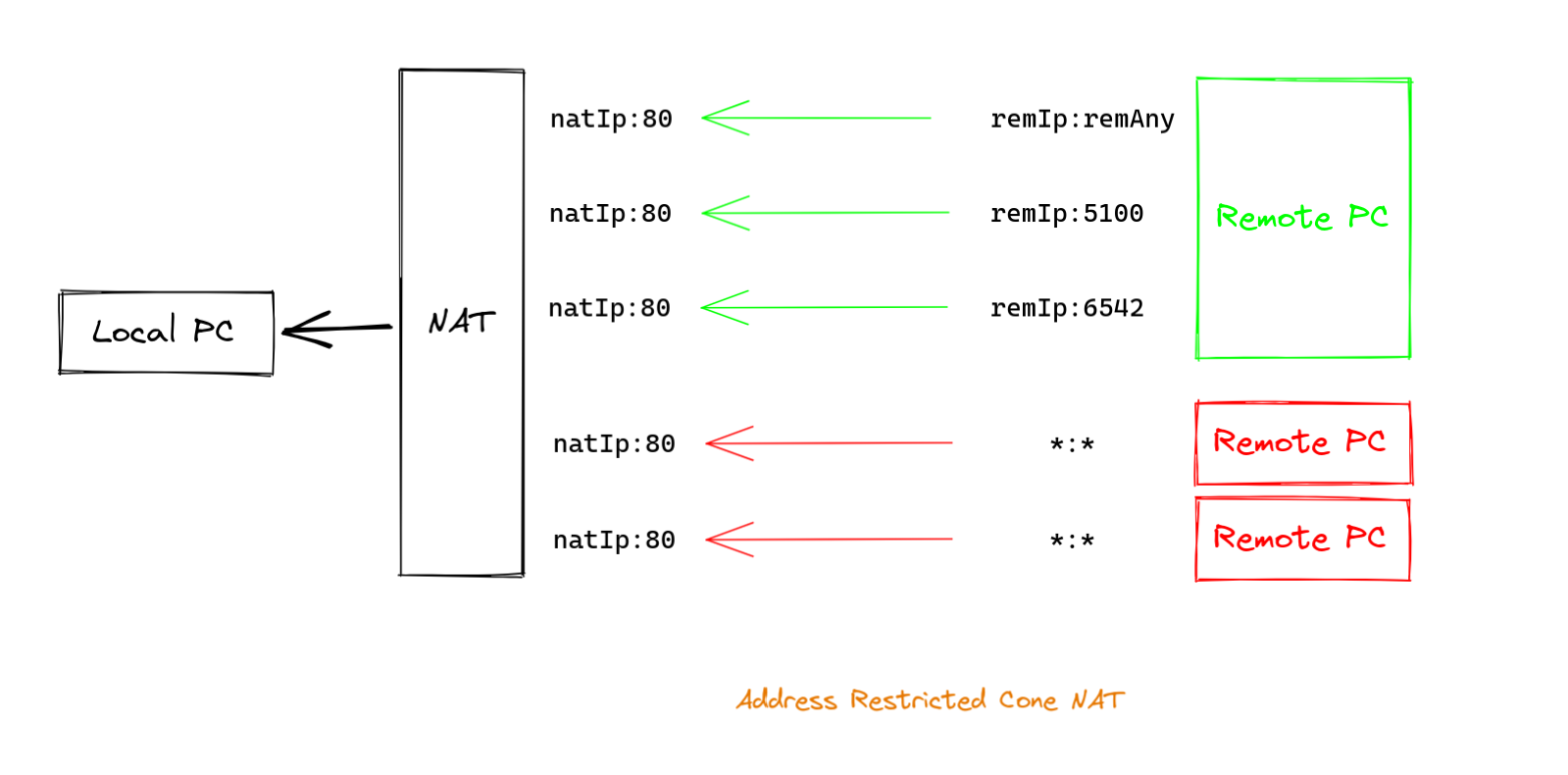 Image 3. The Address Restricted Cone NAT allows traffic only when the local PC has previously sent data to the Remote PC
Image 3. The Address Restricted Cone NAT allows traffic only when the local PC has previously sent data to the Remote PC
Port Restricted Cone NAT
Like every article on NAT types, I'll tell you the same: the
Port Restricted Cone NAT is similar to the Address
Restricted Cone NAT but adds another restriction. And also this
NAT type also depends whether we've already sent a packet to the
1remote host as shown in image 1. This NAT type also adds a check
to the PORT number that is used. When you look at image 1 again,
you see that the local PC sends a packet to the remote IP on port
5100, i.e. remIp:5100. By sending this package the NAT creates
an mapping from locIp:locPort to remIp:1500. With a Port
Restricted rule the remote PC can only send data to the local PC
when it sends them from remIp:1500.
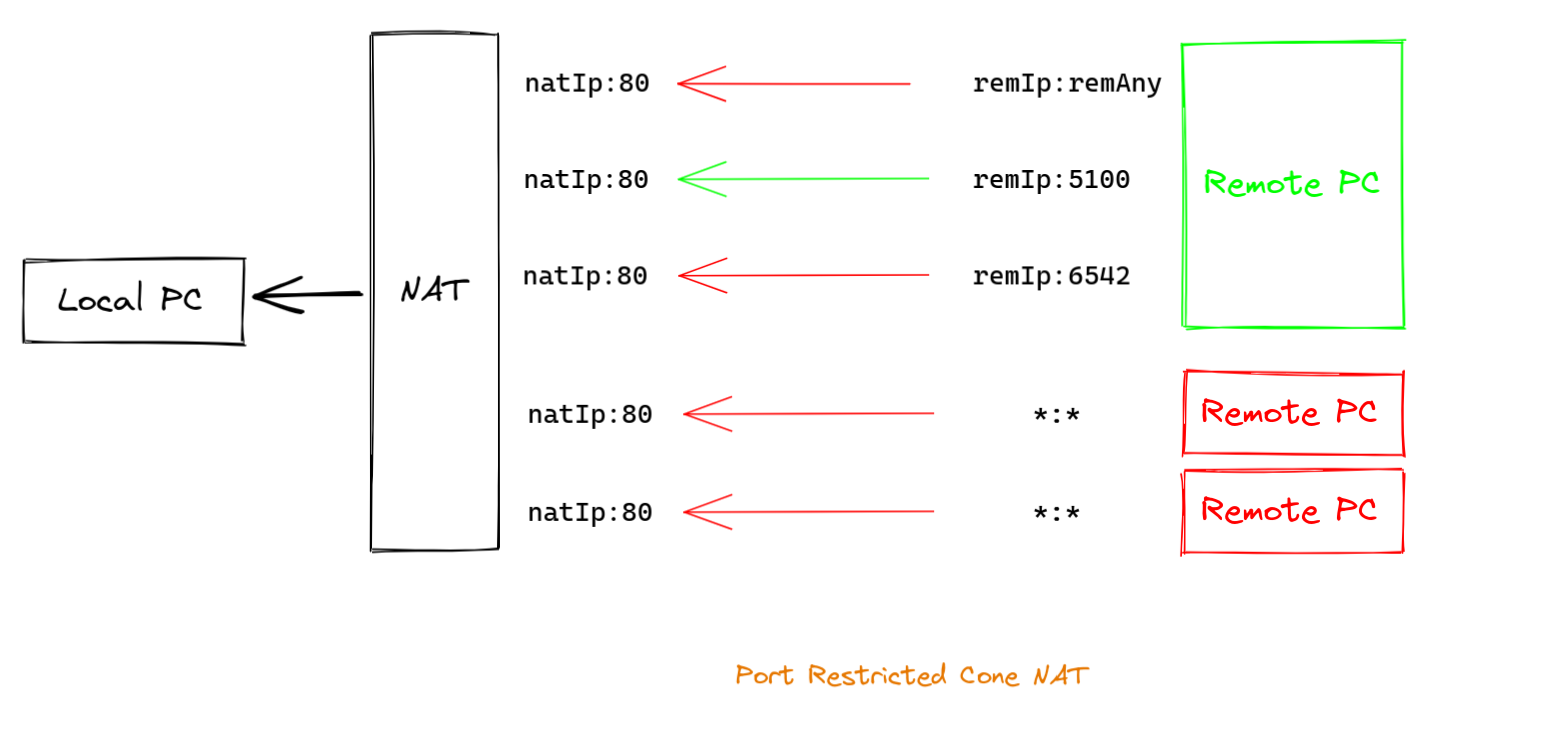 Image 4. Port Restricted Cone Nat: the local PC can only receive data from remote IP:PORT when it previously sent a packet to remote IP:Port
Image 4. Port Restricted Cone Nat: the local PC can only receive data from remote IP:PORT when it previously sent a packet to remote IP:Port
Symmetric NAT
The Symmetric NAT is the most restrictive type of the NAT
types described in this article. A Symmetric NAT will create a
1:1 mapping for each locIP:locPORT to remIP:remPort that is
created. This means that when the local PC connects to a remote
PC on port A and B, it will create two mappings. The RFC3489
describes this very well:
A symmetric NAT is one where all requests from the same internal IP address and port, to a specific destination IP address and port, are mapped to the same external IP address and port. If the same host sends a packet with the same source address and port, but to a different destination, a different mapping is used. Furthermore, only the external host that receives a packet can send a UDP packet back to the internal host.

 NAT Types
NAT Types
 Building Cabinets
Building Cabinets
 Compiling GStreamer from source on Windows
Compiling GStreamer from source on Windows
 Debugging CMake Issues
Debugging CMake Issues
 Dual Boot Arch Linux and Windows 10
Dual Boot Arch Linux and Windows 10
 Mindset Updated Edition, Carol S. Dweck (Book Notes)
Mindset Updated Edition, Carol S. Dweck (Book Notes)
 How to setup a self-hosted Unifi NVR with Arch Linux
How to setup a self-hosted Unifi NVR with Arch Linux
 Blender 2.8 How to use Transparent Textures
Blender 2.8 How to use Transparent Textures
 Compiling FFmpeg with X264 on Windows 10 using MSVC
Compiling FFmpeg with X264 on Windows 10 using MSVC
 Blender 2.8 OpenGL Buffer Exporter
Blender 2.8 OpenGL Buffer Exporter
 Blender 2.8 Baking lightmaps
Blender 2.8 Baking lightmaps
 Blender 2.8 Tips and Tricks
Blender 2.8 Tips and Tricks
 Setting up a Bluetooth Headset on Arch Linux
Setting up a Bluetooth Headset on Arch Linux
 Compiling x264 on Windows with MSVC
Compiling x264 on Windows with MSVC
 C/C++ Snippets
C/C++ Snippets
 Reading Chunks from a Buffer
Reading Chunks from a Buffer
 Handy Bash Commands
Handy Bash Commands
 Building a zero copy parser
Building a zero copy parser
 Kalman Filter
Kalman Filter
 Saving pixel data using libpng
Saving pixel data using libpng
 Compile Apache, PHP and MySQL on Mac 10.10
Compile Apache, PHP and MySQL on Mac 10.10
 Fast Pixel Transfers with Pixel Buffer Objects
Fast Pixel Transfers with Pixel Buffer Objects
 High Resolution Timer function in C/C++
High Resolution Timer function in C/C++
 Rendering text with Pango, Cairo and Freetype
Rendering text with Pango, Cairo and Freetype
 Fast OpenGL blur shader
Fast OpenGL blur shader
 Spherical Environment Mapping with OpenGL
Spherical Environment Mapping with OpenGL
 Using OpenSSL with memory BIOs
Using OpenSSL with memory BIOs
 Attributeless Vertex Shader with OpenGL
Attributeless Vertex Shader with OpenGL
 Circular Image Selector
Circular Image Selector
 Decoding H264 and YUV420P playback
Decoding H264 and YUV420P playback
 Fast Fourier Transform
Fast Fourier Transform
 OpenGL Rim Shader
OpenGL Rim Shader
 Rendering The Depth Buffer
Rendering The Depth Buffer
 Delaunay Triangulation
Delaunay Triangulation
 RapidXML
RapidXML
 Git Snippets
Git Snippets
 Basic Shading With OpenGL
Basic Shading With OpenGL
 Open Source Libraries For Creative Coding
Open Source Libraries For Creative Coding
 Bouncing particle effect
Bouncing particle effect
 OpenGL Instanced Rendering
OpenGL Instanced Rendering
 Mapping a texture on a disc
Mapping a texture on a disc
 Download HTML page using CURL
Download HTML page using CURL
 Height Field Simulation on GPU
Height Field Simulation on GPU
 OpenCV
OpenCV
 Some notes on OpenGL
Some notes on OpenGL
 Math
Math
 Gists to remember
Gists to remember
 Reverse SSH
Reverse SSH
 Working Set
Working Set
 Consumer + Producer model with libuv
Consumer + Producer model with libuv
 Parsing binary data
Parsing binary data
 C++ file operation snippets
C++ file operation snippets
 Importance of blur with image gradients
Importance of blur with image gradients
 Real-time oil painting with openGL
Real-time oil painting with openGL
 x264 encoder
x264 encoder
 Generative helix with openGL
Generative helix with openGL
 Mini test with vector field
Mini test with vector field
 Protractor gesture recognizer
Protractor gesture recognizer
 Hair simulation
Hair simulation
 Some glitch screenshots
Some glitch screenshots
 Working on video installation
Working on video installation
 Generative meshes
Generative meshes
 Converting video/audio using avconv
Converting video/audio using avconv
 Auto start terminal app on mac
Auto start terminal app on mac
 Export blender object to simple file format
Export blender object to simple file format